![]()
KEY ON DEMAND ENCRYPTION
EASY ENTERPRISE FILE ENCRYPTION
SECURE ENTERPRISE KEY SHARING
What is KODE?
KEY ON DEMAND ENCRYPTION
Generates The Keys
Hassle-free! No more creating keys. KodeFile generates a random, secret AES 256-bit encryption key for every file.
Stores The Keys
Worry-free! No more forgetting keys. "Separate the lock from the key" security. You have the files; KodeFile has the keys.
Shares The Keys
Stress-free! No more exchanging keys. Upon request, KodeFile shares the keys with your confidants and decrypts the files.
Agents Encrypt Your Files
Invite your work force to join KodeFile and become the encrypting Agents of your Enterprise. Organize Agents into hierarchical Inner-Circles with restricted membership and customizable key settings.
Independently Store & Share Files
Your Agents manage, store and share your files, separate of KodeFile. Perfectly complements your Enterprise's existing file management, email and cloud services. KodeFile never possesses your files.
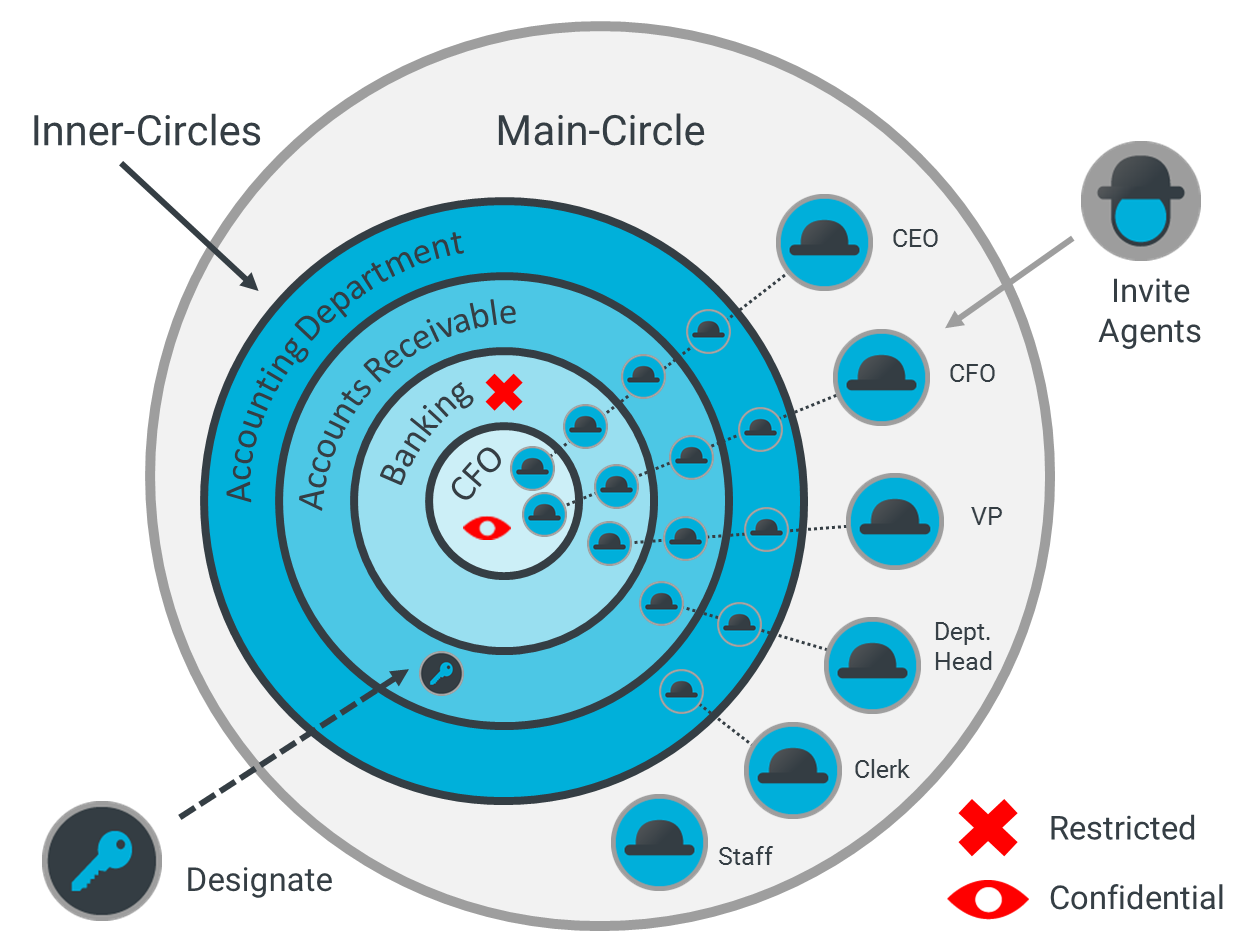
Enterprise-Owned Keys
During encryption, Agents designate an Enterprise Circle to be the Key Owner of the files. This designation ensures the keys always remain under the Enterprise's ownership and control, regardless of the encrypting Agent.
Share Your Keys
Ideal for collaboration, Circle keys are available to all Circle members for decrypting. If necessary, Agents share the keys with members outside the Circle or Enterprise. Agent make a mistake? Unshare the keys.
Put Your Agents To Work Protecting Your Files
Gain Security
It's not a case of if, but when your Enterprise will be hacked. With a few clicks, encrypt your Enterprise's most critical files.
Gain Expendiency
Safely share sensitive documents. Email encrypted files. Save time and postage. Audit trail: decrypted = delivered.
Gain Control
Store with confidence and utilize your cloud to the fullest. Upload encrypted files. Share or unshare the keys as necessary.
Endless Encryption Use Cases Across All Industries
Financial Houses
Store transaction and consumer data. Industry Compliant
Law Firms
Email private contracts and client files. Privilege Compliant
Medical Practices
Upload patient records and lab results. HIPAA Compliant
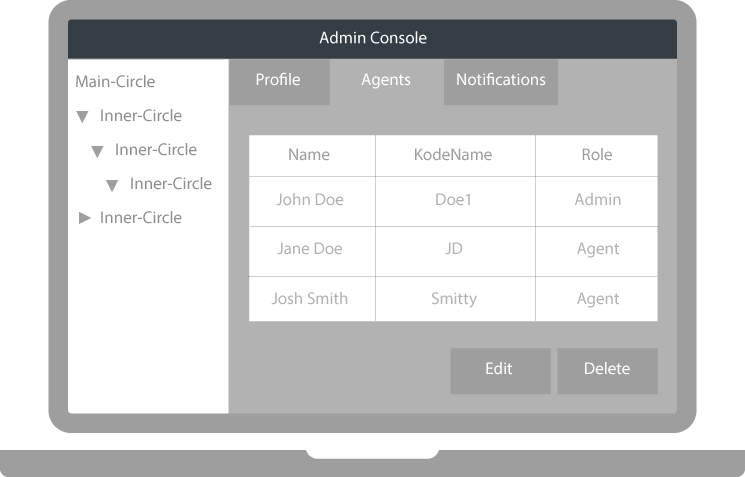
Easily Administer Your Keys
New Agent? Add to any Circle and they immediately gain access to keys. No need to individually share keys for past files.
Oversight
Collaborating Agent? Restricted Inner-Circles ensure keys are never shared outside the Circle. Ideal for sensitive group projects.
Security
Rogue Agent? Unshare all the keys ever shared by an Agent. No longer fear your employees stealing or losing encryption keys.